Design Project
From CSSEMediaWiki
(Difference between revisions)
m (→Description) |
m (→Description) |
||
| Line 42: | Line 42: | ||
=== Description === | === Description === | ||
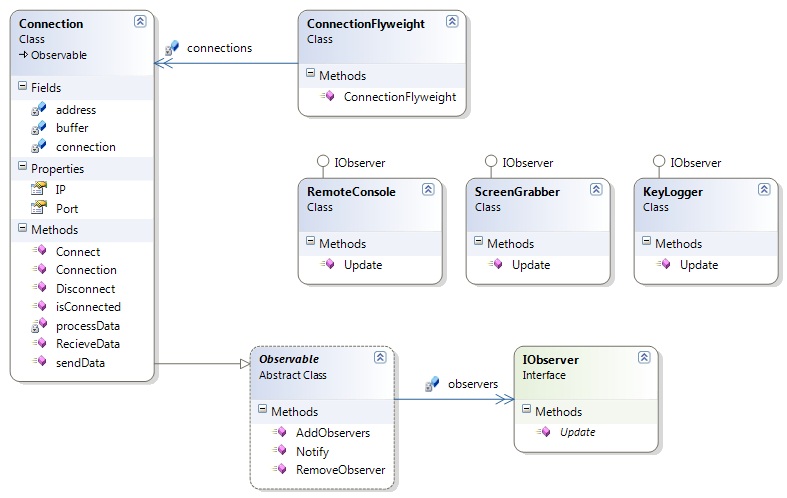
| − | [[Image:Commander.jpg| | + | [[Image:Commander.jpg|centre|frame|Figure 1 : Commander Project Class Diagram]] |
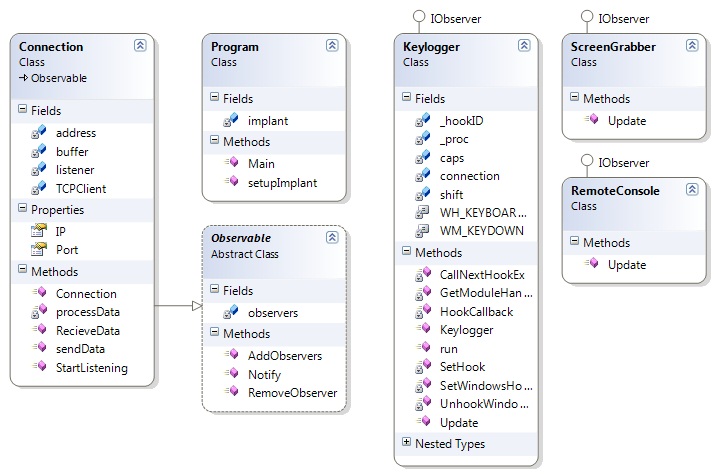
| − | [[Image:Implant.jpg| | + | [[Image:Implant.jpg|centre|frame|Figure 2: Implant Project Class Diagram]] |
=== Justification === | === Justification === | ||
Revision as of 12:07, 23 September 2009
Contents |
COSC427 Design Project
Introduction
As a joint project Douglas Wall and I are developing an Implant and Controller for the Information Warfare course COSC429. This project will be topic of my COSC427 design project. The project consists of an application which allows nefarious activities to be performed on a target machine from the comfort of a separate machine. These activities could include,
- Keylogging
- Screen Grabbing
- Remote access to a command prompt.
- Stealing files
- Executing code
The project is to be developed for Windows operating systems. It will be coded in C# and is being developed in Visual Studio 2008. We intend to code using Test Driven Development.
Requirements
More specifically, we wish to achieve the following in our project,
| ID | Requirement | Description |
| 1 | Keylogging | Recording and storing the keystrokes of the victim |
| 2 | Screen grabbing | Taking one or many screenshots of the victims computer and storing them |
| 3 | Remote command prompt | Getting access to the command prompt which will allow browsing of the computer, the deletion and adding of files, running executable code and so on. |
| 4 | Multiple implant management | Allowing more than one victim to be managed by one implant. |
| 5 | Data analysis | Automated screening of data from keylogging and screen grabbing activities to search for interesting information such as passwords. |
| 6 | Command line interface | The controller can be used through the command line. |
| 7 | Graphical user interface | The controller has an intuitive, tidy GUI. |
| 8 | Stealing files | The controller can select a file from the victim and download it to the controller computer. |
Design (1)
Description
Justification
Critique
Summary and Learning
Design (2)
Design (3)
Draft Notes - Please Ignore
* What is this project * What specifically are our requirements * What is the language and development tools * What are the intial design sketches * Why have I chosen that initial design * What is wrong with that design * Continued iterations of the design with justifications