Nelson Shaw Design Project
Contents |
Trojan Project
As part of the COSC429 Information Warfare course, development of a Trojan module is required.
The software should have command and remote modules, which are connected together via sockets. Functionality such as screen capture, key log capture and remote file browsing is required.
A more formal description is shown below.
Design Study
A current log of work spent on the project can be found here Design Project Log
Requirements
- Secure - Components and communication of software should be secure and unable to modify
- Maintainability - Easy to add new functionality (e.g. Multiple remote modules)
- Extensible - Add additional software components easily (e.g. Software to deliver remote module onto target system)
Constraints
Remote and control module communication, processing speed and associated overhead costs.
Initial Design
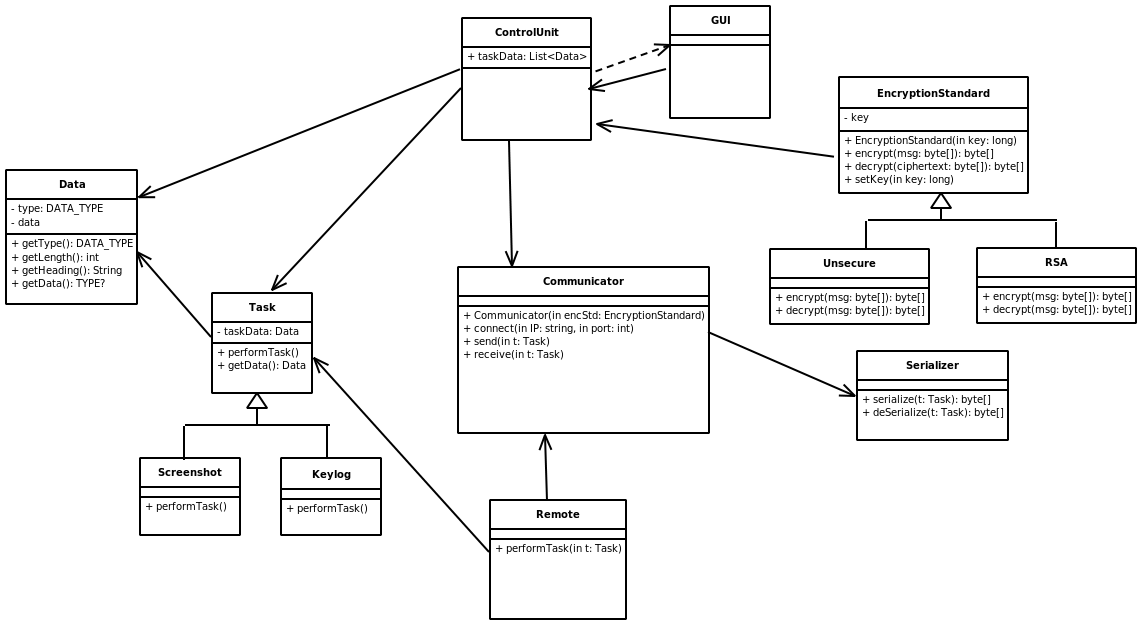
This is my current UML diagram -- a work in progress.
Description of Classes
Controller is the main class of the control module. An observer pattern is used with the GUI and Controller. Communicator is used to set up a connection between the control and remote modules. The type of encryption can be set, and some design is still required in terms on the encryption mechanism.
A considerable design issue is the idea of tasks that the module can perform. At the moment, various implementations of a task can be created using sub classing. At the moment this design is not optimal and future refinement is intended.
Data is a class that is intended will carry information between the modules.
Design Critique
Criticism of design goes here.
Design Improvements
Possible improvements.
Thanks to User: James Ashford for the project page template.